What is Cross-site Scripting?
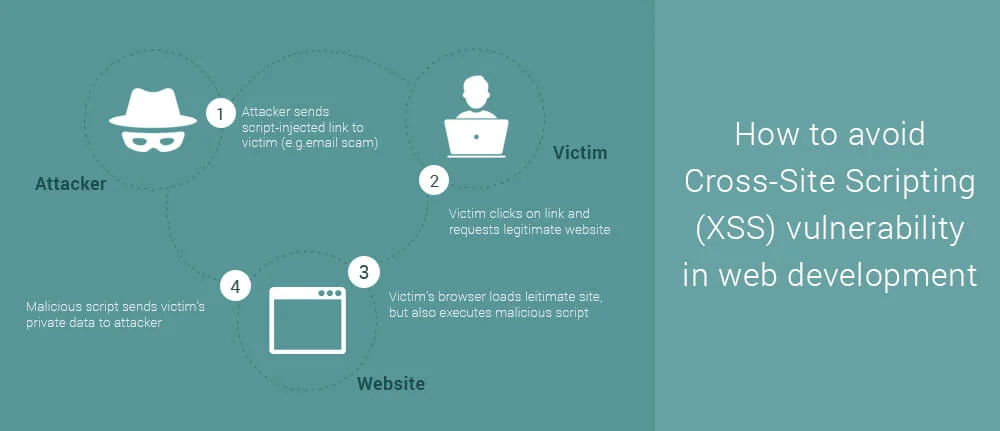
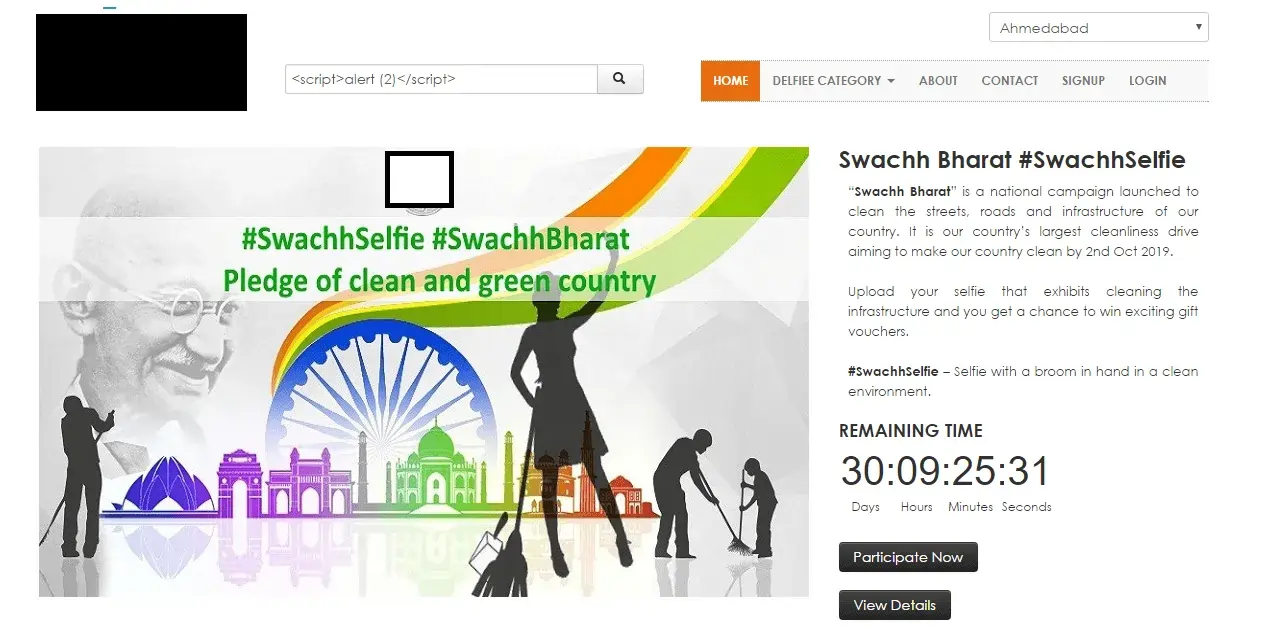
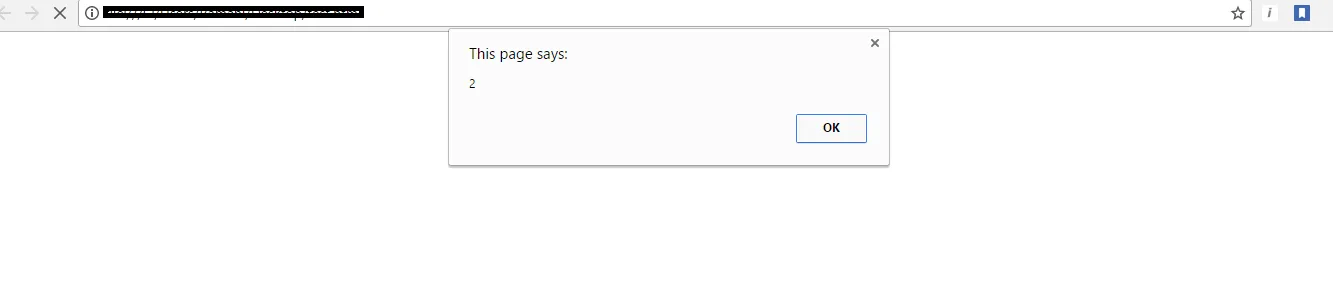
Cross-site scripting attacks are types of injection, in which malicious scripts are injected into trusted web applications. This attack happens when a hacker uses web application to send infected code, many times in the form of a browser side script to the remote end user. Flaws which allow these attacks to succeed are widespread and can occur anywhere. A website uses input from a user and within an output it generates without encoding or validating it.
An attacker uses XSS to send a malicious script to victim. The end user’s browser doesn’t have any way to know the trustworthiness of the script. The user believes that the script has come from trusted source so he executes it. The malicious script in it gets all the sensitive information retained by browser like session id, tokens, cookies, etc. These kinds of scripts even rewrite the content of HTML page.