How can you know you are vulnerable?
Here are some easy ways to find out if your web application is vulnerable or not.
-
Does the application verify the exact user and the resources he is given access to? (For all direct references to restricted resources)
-
Suppose the reference is an indirect reference, you need to verify if the mapping to the direct references fail to restrict the values for authorized current user.
Code review of any application by custom web application companies can identify whether we can apply either approach safely or not. In most of the cases manual testing is proved to be effective to identify direct object references and check whether they are safe or not. Automated tools generally cannot look for such flaws as they cannot distinguish protection what is safe and what is not.
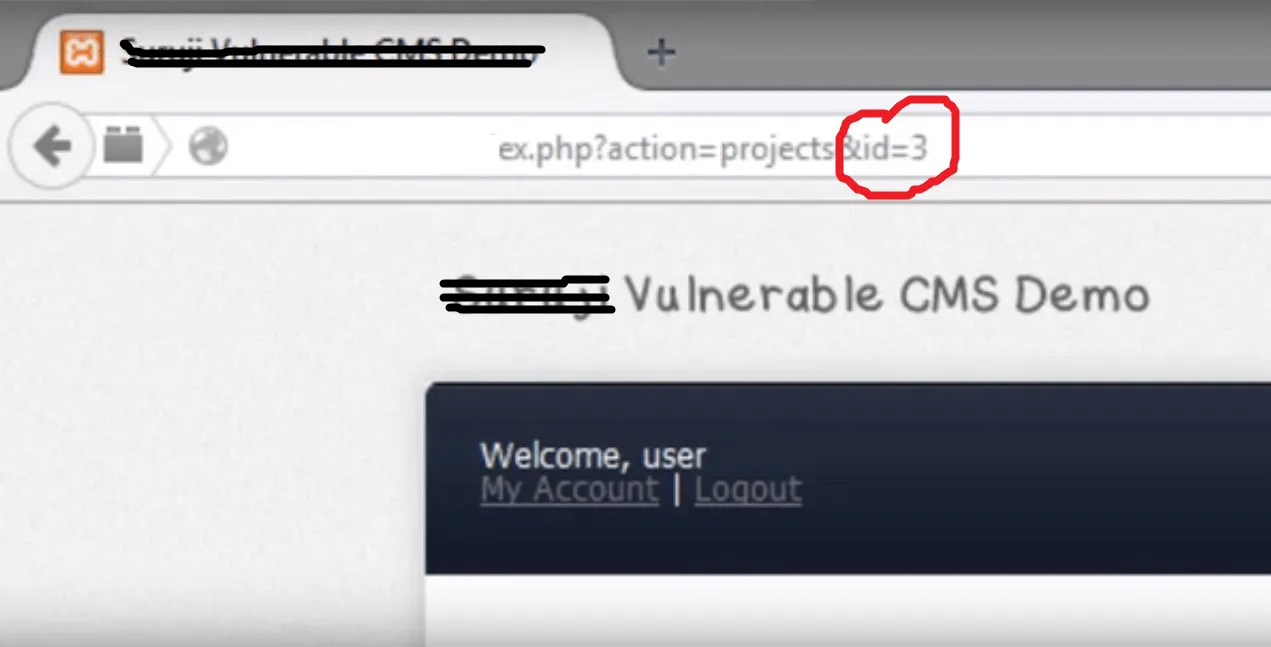
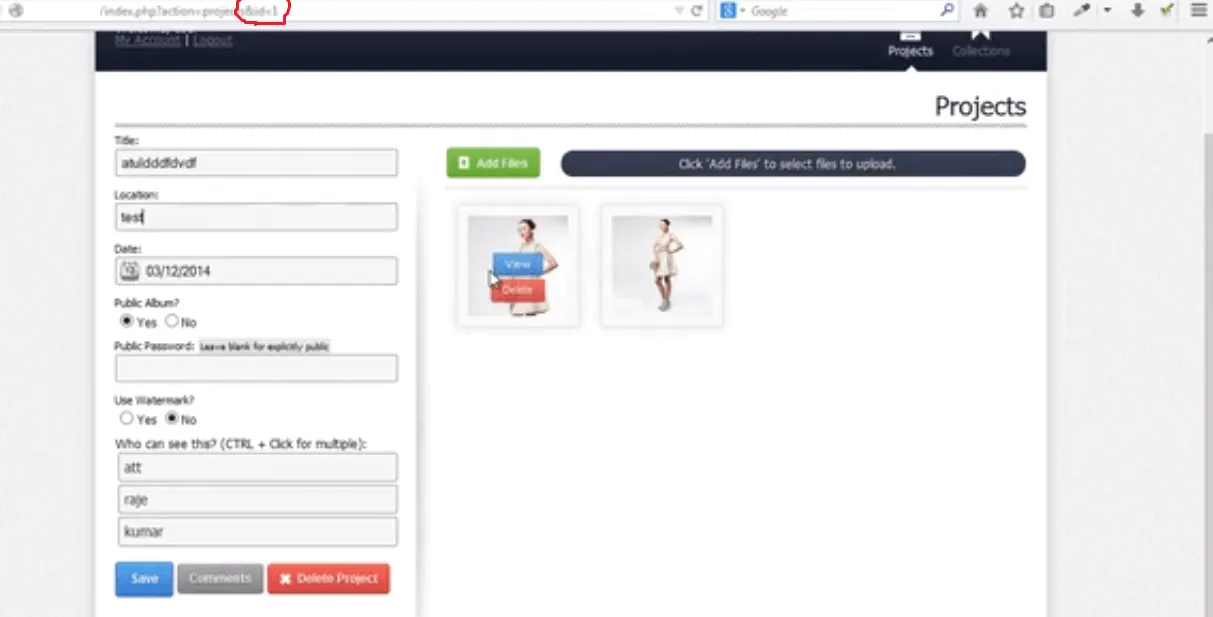
Let’s have a demo website where an object id is 3 which can be seen like this.
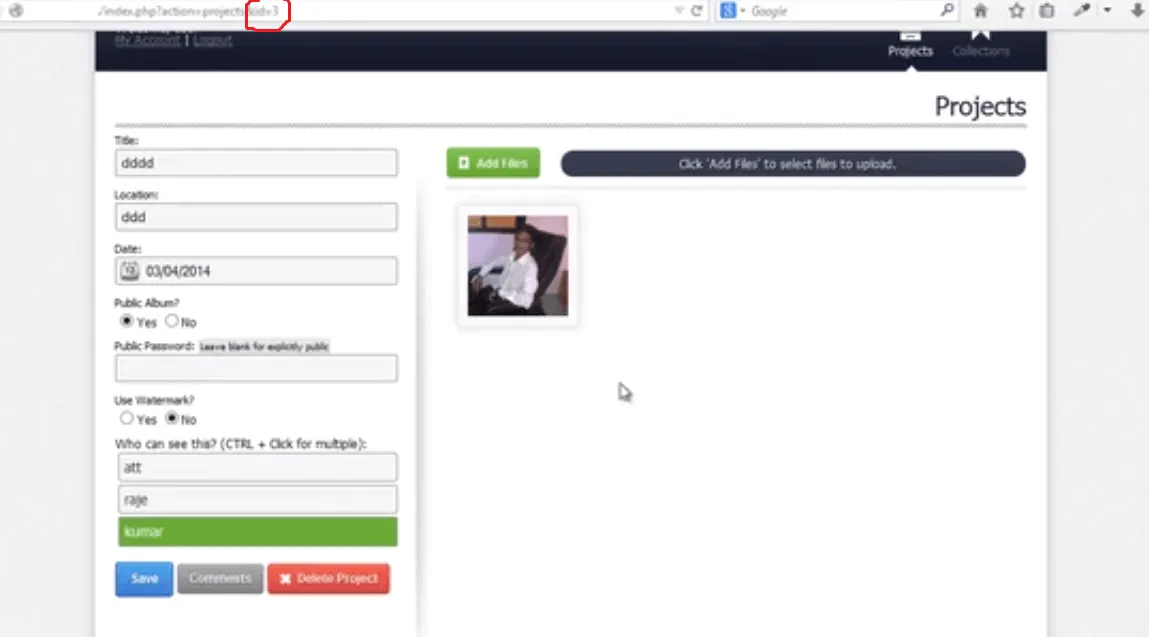
Here is the object (A user profile)
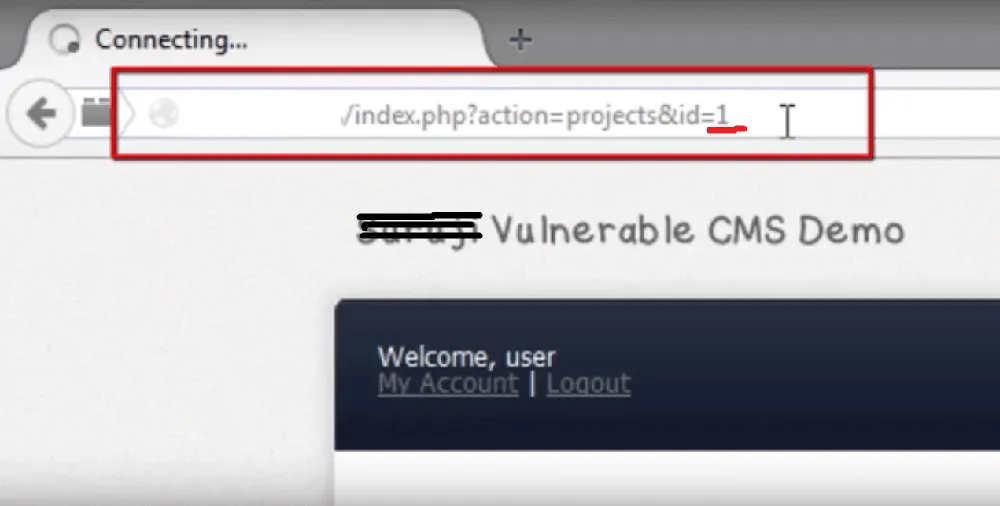
Now if we just change id from id=3 to id=1 in URL, we can see that we are directly given access to that object on id=1.
Severity:Medium