Our Insights
Innovative Ways - Satisfied Clientele

We use cookies to improve your experience on our site. Please accept cookies for optimal performance.

601 & 612, The Times square Arcade, Near Baghban party plot, Thaltej - Shilaj Road, Thaltej, Ahmedabad, Gujarat - 380059
Request For a Free Consultation
Innovative Ways - Satisfied Clientele

Kapil Panchal - December 28, 2021
Today, the world without transportation and software is just difficult to imagine. Isn’t it? Because without these two, neither vaccines could have been delivered successfully nor Pfizer have become the leading sterile injectable supplier in 2021. The transportation and logistics industry has experienced a drastic change in its operations due to the integral role of emerging technologies. The growing popularity of custom software development has substantially impacted this industry by simplifying...
Kapil Panchal - December 24, 2021
The expanding role of technologies and seamless digital transformation has dramatically reshaped the banking sector. As finances are the main base for any business, a sophisticated system is necessary to manage financial transactions with complete clarity and accuracy. The growing popularity of digital payment systems created huge challenges for financial businesses in case of security and reliability. One such technology that benefits businesses with enhanced security and agility is SaaS,...

Kapil Panchal - December 21, 2021
There has been a dramatic change in the style of “selling and purchasing” business. All this happens as an effect of the technological advancement that the world is experiencing today. E-commerce is one of the trends in business and what makes this so amazing is that it offers the best kind of solutions for all your needs. Businesses can make deals for sales and purchases in just a few clicks. Online presence has become indispensable for any e-commerce business and to stay competitive, it...
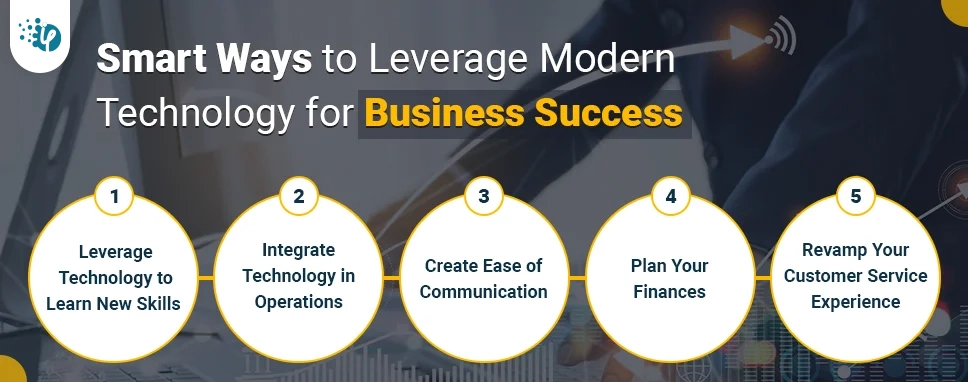
Kapil Panchal - December 16, 2021
[source : pixabay ] The start of a new decade brought along some massive changes. Businesses around the world had to bear heavy losses. If you are someone who owns a small business, you were likely on the verge of giving up during early 2021. But there were some businesses that not only sustained but thrived during the pandemic. So what is it that they did differently? While some businesses shifted their focus area to the online marketplace, others went on to start a new culture...
Recent Posts

Ethical Considerations for Using AI in Healthcare Software
February 03, 2026


How to Do Forecasting in Power BI (Steps & Accuracy Metrics)
December 02, 2025

ETL vs ELT: Key Differences, Benefits & Use Cases Explained
November 26, 2025

Modernizing applications with the 7 R strategy – A CTO’s Guide
October 16, 2025
Categories

