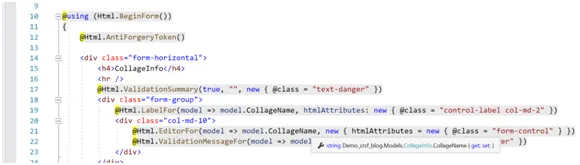
CSRF stands for Cross-site request forgery. CSRF is also known as the one-click attack which is used for Security purpose. It is an act of copying or imitating things like a signature on a cheque, official documents to deceive the authority source for financial gains. Cross-site request forgery is a web security Weak that allows an attacker to induce users to perform actions that they do not intend to perform.
Cross-site request foreign is generally described in relation to cookie-based session handling, it also arises in other contexts where the application automatically adds some user credentials to requests, such as HTTP, HTTPS, FTP Basic authentication, and certificate-based authentication.
To preclude Cross-site Request Foreign attacks, use anti-forgery tokens with any authentication protocol where the browser silently sends credentials after the user logs in. This includes cookie-based authentication protocols, such as forms authentication method authentication, as well as protocols such as Basic and Digest authentication
First of all, we discuss how Spring Security can protect applications from CSRF attacks, we'll explain what a CSRF attack is. Let's take a glance at a concrete example to urge a far better understanding.
Assume that your bank's website provides a form that permits transferring money from the currently logged in user to a different checking account. For instance, the HTTP request might look like:
POST /transfer HTTP/1.1
Host: bank.example.com
Cookie: JSESSIONID=randomid; Domain=bank.example.com;
Secure; HttpOnly
Content-Type: application/x-www-form-urlencoded
amount=100.00&routingNumber=1234&account=9876
You can pretend your authentication to your bank's website then if without logging out, visit an evil website. The evil website contains an HTML page with the subsequent form that looked like this.
You like to win money, then you click on the submit button. within the process, you've got unintentionally transferred $100 to a malicious user. It’s just a fraud.
This whole process could be automated using JavaScript. This suggests you didn't even get to click on the button. Then how can we protect ourselves from such attacks?