Testing for SQL Injection
Using the Burp suite to Test Security Misconfiguration Issues
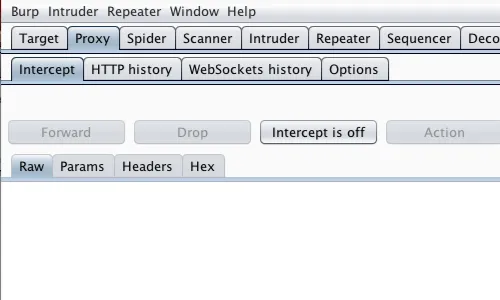
Firstly ensure that burp suite is configured to your browser
Keep intercept off in the Proxy tab
Now open the page of the web application you want to test.
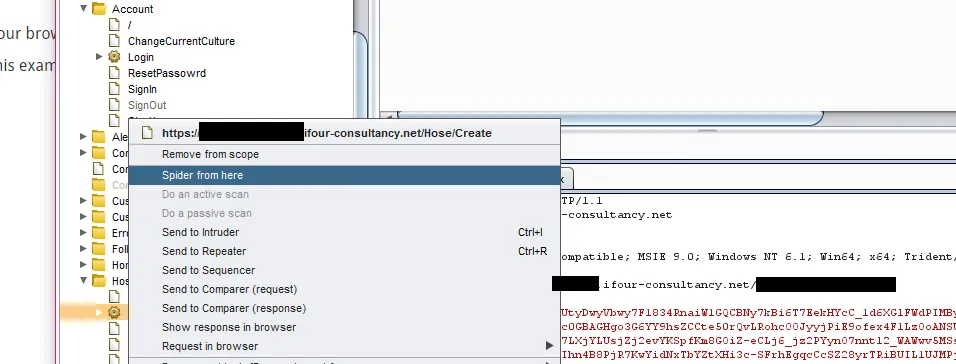
Now go to burp and select the ‘target’ tab and click on ‘site map’
Locate your application’s name there and choose one of the directories randomly whic the user can access in the application. Here eg. Add attachment.
Click on the link and press spider the branch.
Select one of the directories from the ‘site map’ and explore further.
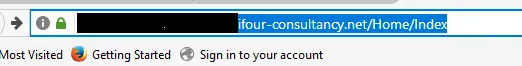
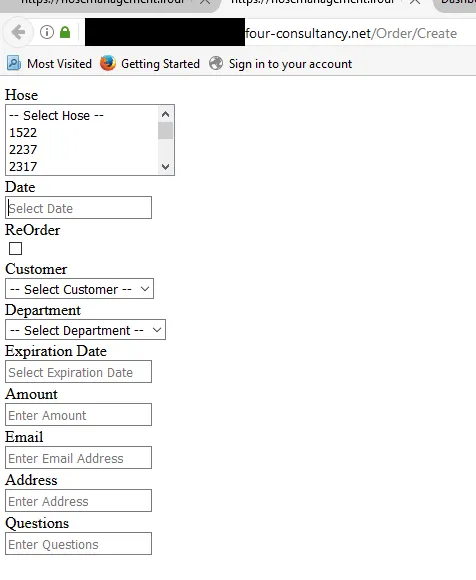
Return to the browser and add the name of the directory to the URL eg.: https://...../addattachment/
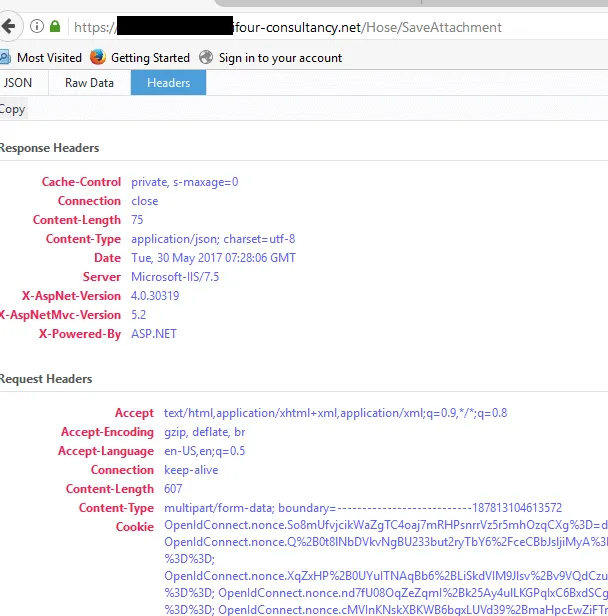
Explore all the links, files and directories you are able to find.
Here you will see that the details of the server and other unnecessary information are displayed in the error message which could be a hole for the attacker to attack the system further.