4 Types of Healthcare Analytics with Examples & Success Stories
You already know how healthcare creates tons of clinical data every day. Patient visits… Labs… EMRs… doctor portals… scheduling systems… everything is generating numbers nonstop. But...
Our customer is a reliable software development company in USA with branches in Greater Detroit and in Indianapolis area. It offers full spectrum of IT consulting services to its clients and help them achieve their business goals.
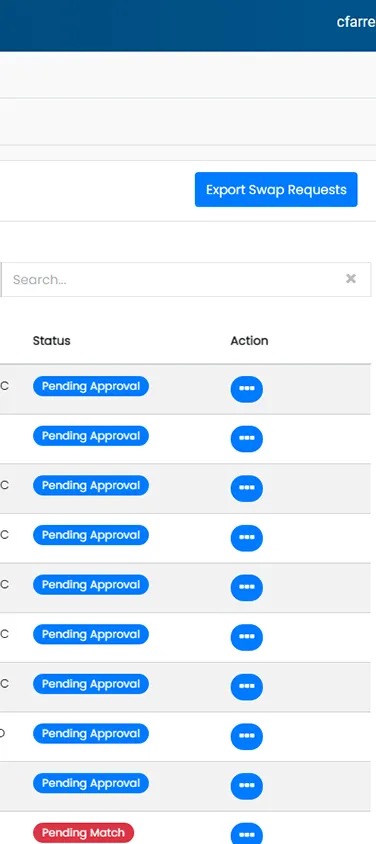
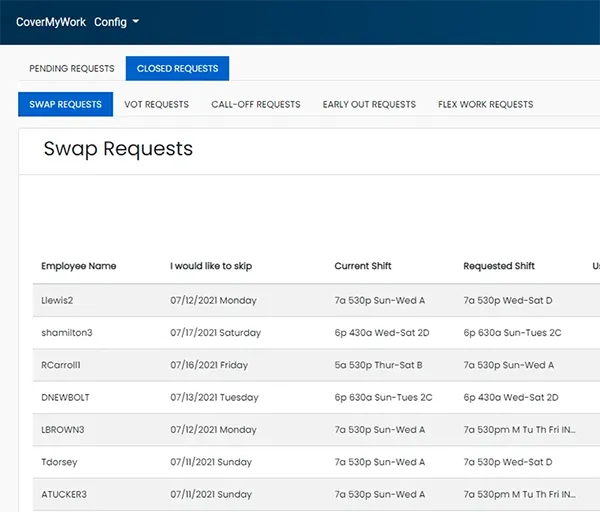
In any organization, it is difficult for managers to create and manage schedules, given people’s preferences and availability, especially while working in shifts. This problem gets exacerbated when faced with shift swap requests, sick calls, no-shows, etc. This creates a need for permitting swap shifts among the staff.
We encourage you to contact us with any questions or comments you may have.

iFour Technolab Pvt. Ltd., a leading sustainable IT services and solution provider in the USA, has come up with a robust application to cope with the above concerns. The system has the following features:
Role-based access control – Role-based access control – Quick, secure and easy access control. When logged in with the appropriate credentials, the user gets authenticated and redirected to the page.
Users’ role
Manager’s role
HR team
Purchaser
Administrator – During the initial implementation, the organization needs to set up its new information into the system and conduct the initial configuration level set up.
Learning admin
Scheduling – This system has many cron jobs running to improve the performance of end users. So, whenever any action is initiated, it creates an enqueuer job that executes in queue to increase performance. For instance, sharing SMS, email for each request, monthly auto-invoicing, big data import, etc.
In some organizations, it is difficult to maintain employee data in a non-digital form. In such cases, this system would be very helpful for faster workflow execution. This solution helps managers to dynamically address demand fluctuations by matching workforce scheduling. Moreover, the customer does not have to provide any new hardware.
Running a freelance business is more than just being a contractor with an LLC. To build a sustainable business, you need to recruit talent, establish marketing channels, build a sales pipeline, manage accounts, dispatch work orders, send proposals, manage...
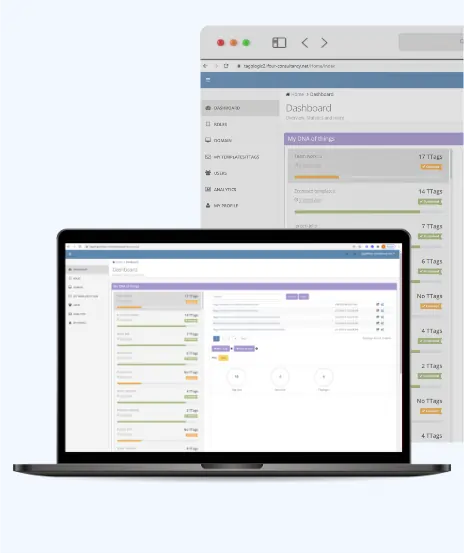
About Customer Customer is an innovator of model that uniquely identifies every physical and logical objects in the world. Customer is based in the Netherlands and has patented this model of uniquely identifying objects. Unique identifier specifies...
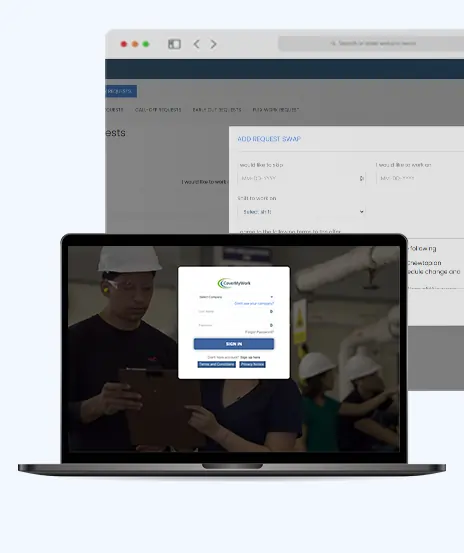
In any organization, it is difficult for managers to create and manage schedules, given people’s preferences and availability, especially while working in shifts. This problem gets exacerbated when faced with shift swap requests, sick calls, no-shows,...

About Customer Customer is a leading consultant in United States that has a focus to bring about an innovative online platform that provides a place for hang out with different people. It is achieving a huge potential of growth and prosperity...

About Customer Customer is a leading Gujarati media company in India engaged in Gujarati movies production, theatres and casting artists for various movies and projects. Customer has experience producing many prominent Gujarati movies and serials....

About Customer The customer is a leading business consulting firm in business process analysis, project management and software outsourcing. It needs a good project management software and wants to build an earned value management (EVM) software application...
See how we've transformed businesses with Azure cloud solutions
You already know how healthcare creates tons of clinical data every day. Patient visits… Labs… EMRs… doctor portals… scheduling systems… everything is generating numbers nonstop. But...

Let’s keep it simple. In healthcare, trust, safety, and human dignity come first, no matter what solution you build. The same applies to AI. Today, it is everywhere, from clinics...

Let's keep it real. The whole point of building autonomous Agents is to cut manual work and keep focus on business. Approvals that used to take days can happen in hours because...