4 Types of Healthcare Analytics with Examples & Success Stories
You already know how healthcare creates tons of clinical data every day. Patient visits… Labs… EMRs… doctor portals… scheduling systems… everything is generating numbers nonstop. But...
The customer is a well-known training and development service provider in Australia that offers training on various computer courses such as MS Excel, MS Office, SQL, Xero, PHP, HTML, CSS, JavaScript, jQuery, and many more. They have helped several clients, both corporate and government with cost-effective training and development services.
Managing operations while nominating and electing executives for the building voting process was a difficult and time-consuming task. Keeping a transparent voting process, maintaining confidentiality and security is quite challenging. To overcome the confidentiality issue and automate the voting process, our customer realized the need to develop a reliable and sustainable system for building a voting process which could offer resilient features to the users.



We encourage you to contact us with any questions or comments you may have.

iFour Technolab Pvt. Ltd., a leading .NET development company in USA, materialized customer concept with a web-based application that automates the building voting process.
iFour Technolab offers high-quality custom software solutions to various industrial domains. Clients can hire Node.js developers , WPF developers, Angular experts, Blockchain developers to cater to the needs of their business.
The system offers the following features.
Secure registration for users and strata managers
"Creation, Maintenance and Monitoring" of an AGM (Annual General Meeting) includes owners and general public attendance, registration of proxy voters, registration of executives
Generation of the paper-based vote, creation of encrypted URL for vote validators to enter the votes, send URL via email or SMS to vote validators managed by the strata managers
Administrator and Strata manager manages nomination of executives and vote validators for each AGM.
"Creation and Assignment of owners to lots" is handled by the strata managers
"Admin Portal" provides full privileges of the system including administration of strata managers
Strata managers are responsible for "Management of Building Managers and Owners"
Assignment of EC member for building after EC Vote
"Report Generation" module produces dynamic and accurate reports of the results as per the need of the customer
Import/Export functionality provides offline utilization of the reports
With the reliable solution provided by the iFour Technolab Pvt. Ltd., customer was able to automate the entire building voting process. The new system ensured the transparency in voting and confidentiality of the casted votes. The system made the voting process secure by encrypting the voting URL.

About Customer Customer is a leading training provider in Australia. Customer offers various computer programming or Microsoft training courses like MS Excel, MS Office, SQL, Xero, PHP, HTML, CSS, JavaScript, jQuery, and more. Customer is a preferred...

Quick Summary Independent landlords in the U.S. were losing money and visibility to big rental platforms that charged heavy listing fees. Renters, on the other hand, struggled with slow, complex search experiences. This case study shows...
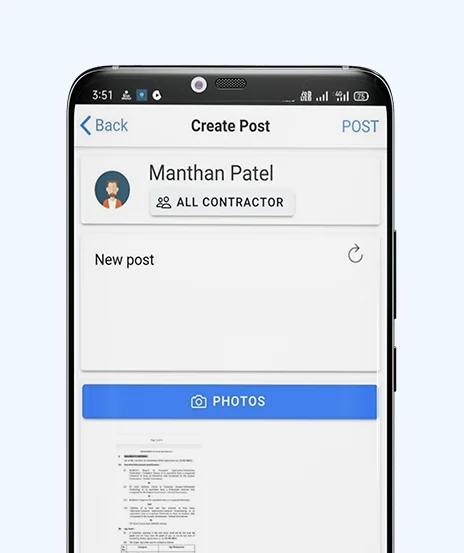
Sometimes contractors face difficulty in finding workers in their area to complete jobs on time. The client was seeking to build a solution where contractors can post their job requirements easily and find workers effortlessly. iFour Technolab has helped...
About Customer Customer is an innovator of model that uniquely identifies every physical and logical objects in the world. Customer is based in the Netherlands and has patented this model of uniquely identifying objects. Unique identifier specifies...
See how we've transformed businesses with Azure cloud solutions
You already know how healthcare creates tons of clinical data every day. Patient visits… Labs… EMRs… doctor portals… scheduling systems… everything is generating numbers nonstop. But...

Let’s keep it simple. In healthcare, trust, safety, and human dignity come first, no matter what solution you build. The same applies to AI. Today, it is everywhere, from clinics...

Let's keep it real. The whole point of building autonomous Agents is to cut manual work and keep focus on business. Approvals that used to take days can happen in hours because...