Many times it happens that you get a link via mail or social media and when you directly click on that link you are fortunately directed towards some wrong website which is not supposed to be. This is an example of Unvalidated redirects and forwards as per software development companies.
Table of Content
- 1. How to find the web application is vulnerable to redirects?
- 2. How actually it looks like?
- 3. Prevention
Unvalidated redirects and forwards is ranked 10th on the list of OWASP top 10 vulnerabilities 2013. In this vulnerability a web application accepts untrusted source which could cause the web application to redirect on any untrusted web application. On modifying that untrusted URL source to a malicious site, the attacker can do any phishing scam and steal any sensitive user data. Here websites many times forward or redirect users to any other web pages and use untrusted data to identify the destination pages. Without any proper validation, attackers redirects victims to malware sites or uses forwards to have the access of unauthorized pages.
How to find the web application is vulnerable to redirects?
Here are best ways to find out if a web application has any unvalidated redirects and forwards or not.
Review the entire code which automatically redirects or forwards. For each redirects, review if target URL has any parameter values. If you find any target URL isn’t validated against whitelist than your application is vulnerable.
Check the site if it generates any redirects. If it does than change the URL target and check whether the site redirects to a new target.
In case code is unavailable, check for all parameters to identify if they seem to be part of a redirect or forward URL and test them.
How actually it looks like?
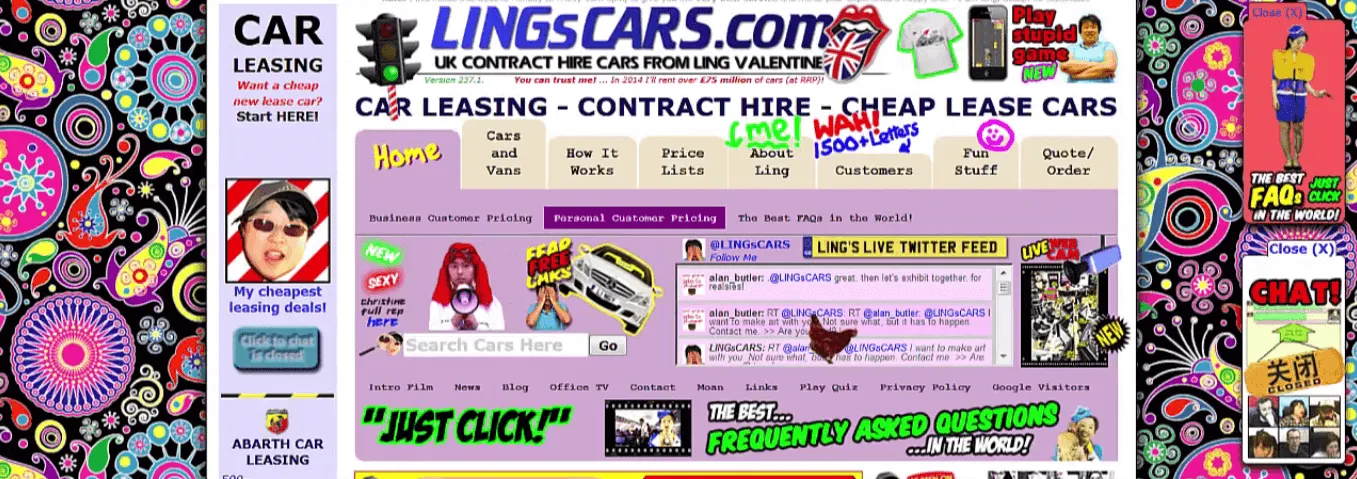
Take an example of an email. Many times it happens that you get a link of any other website in your mail.
According to this link we are supposed to redirect at altoro website. But when we click this link we are redirected to any other website.
Now giving any input to this website may cause to phishing.
Severity: Medium
Prevention:
There are number of ways by which you can prevent this vulnerability from your web application. Safe redirects and forwards can happen in numerous ways.
Try not to use redirects and forwards.
In case you use them, it is advised not to involve user parameters in calculating the destination.
If you cannot avoid destination parameters, make sure that a supplied value is valid as well as authorized for a user.
One Stop Solution for .NET Web Development - Enquire Today
Developers can use ESAPI to override the sendRedirect() method in order to ensure that all redirects destinations are safe. To avoid these kind of flaws is important as they are the frequent targets of phishers which are trying to have user’s trust.