Cross-site scripting is ranked 3rd in the list of OWASP top 10 vulnerabilities 2017. Cross-site scripting are one of the most rampant occurring injection attacks faced by various web application across businesses. That’s why to know the causes of XSS, its impact and prevention is must.
Table of Content
What is Cross-site Scripting?
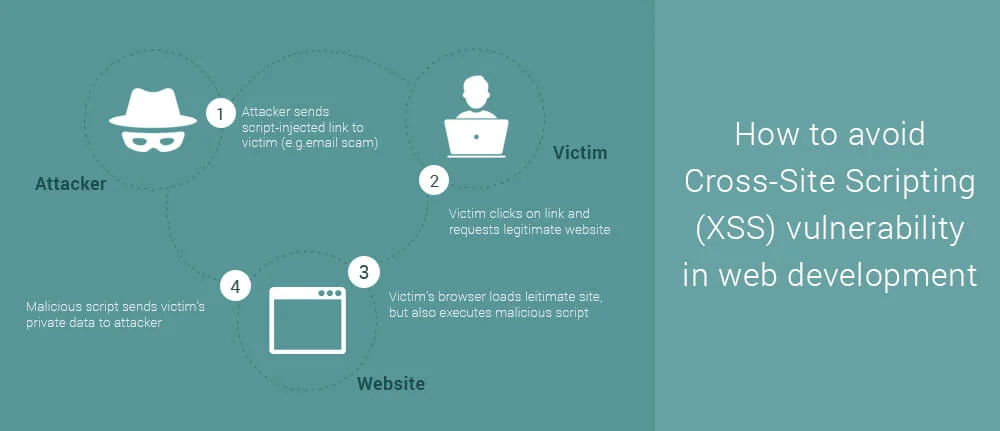
Cross-site scripting attacks are types of injection, in which malicious scripts are injected into trusted web applications. This attack happens when a hacker uses web application to send infected code, many times in the form of a browser side script to the remote end user. Flaws which allow these attacks to succeed are widespread and can occur anywhere. A website uses input from a user and within an output it generates without encoding or validating it.
An attacker uses XSS to send a malicious script to victim. The end user’s browser doesn’t have any way to know the trustworthiness of the script. The user believes that the script has come from trusted source so he executes it. The malicious script in it gets all the sensitive information retained by browser like session id, tokens, cookies, etc. These kinds of scripts even rewrite the content of HTML page.
Types of XSS
Cross-site scripting has three types.
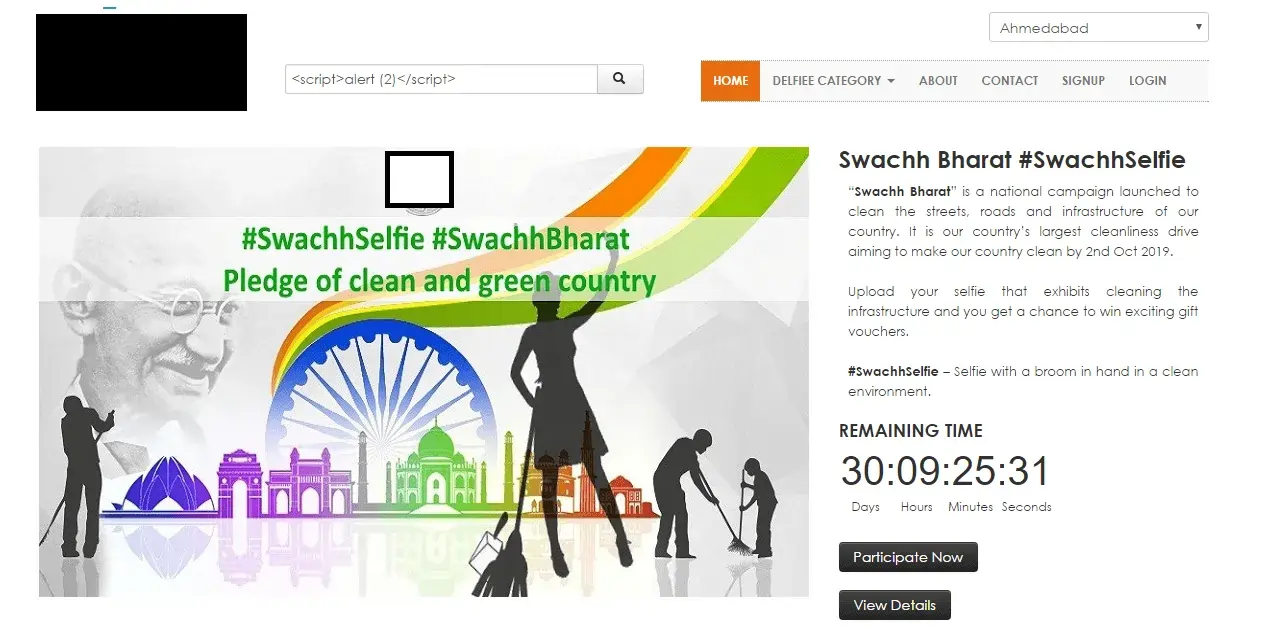
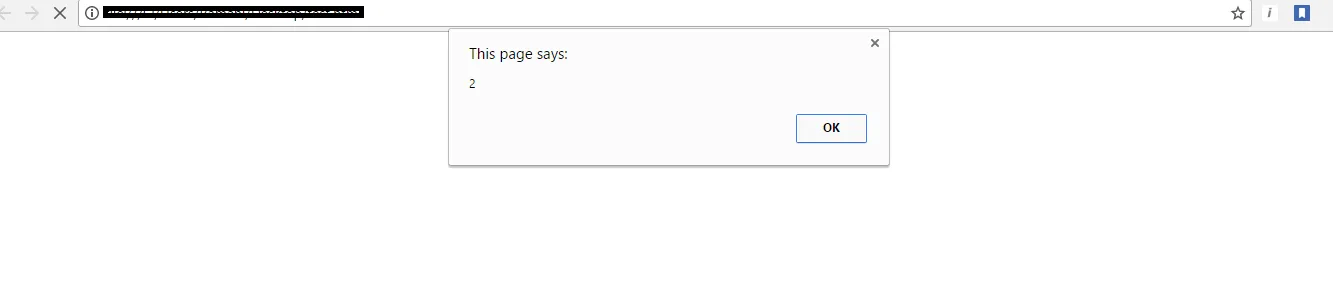
Reflected XSS: An attacker sends a link to a target application through some social media or email. This link contains an embedded script which are executed while visiting script.
Stored XSS: An attacker is able to plant a persistent script into target website which executes when anyone visits it.
Prevention
- To prevent your web application from XSS, you need to separate untrusted data from active browser content.
- It is preferred to properly escape all untrusted content based on HTML context (attribute, body, CSS, JavaScript or URL) which the data would be placed into.
- Positive or whitelist input validation is recommended as it helps protecting against XSS, but it cannot be said as complete defence as many web applications require special characters in their input. Such kind of validation should, validate the length, format, characters, and business rules on that data before accepting input.
- For rich content, refer auto-sanitization libraries for example OWASP’s AntiSamy.
- Refer Content Security Policy (CSP) to protect against XSS for your web application.
Planning to Hire Desktop App Development Company? Your Search ends here.
Conclusion
In today’s world where every industry moving towards digitization, attackers also are keeping owl eyes breaking them in easiest way. A website for a company is the first image for customers. So, it has become mandatory for web developers to take precautions for various web application attacks and making it secured from attackers.